苏州思朋信息科技有限公司2014年02月25日下午16:07新报道显示:苏州思朋CCNA培训基本配置,思朋行业领导者。苏州思朋信息科技有限公司,联系人:何老师,电话:0512-81881012,公司地址:苏州市三香路1298号光大银行大厦16楼B座。
苏州思朋
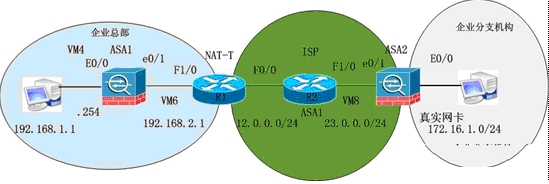
CCNP课程项目综合实验拓扑,这个可是很多项目中要用到的,赶紧好好学会掌握吧!
一、实验拓扑:
二、实验需求:
1:R2路由器模拟ISP服务提供商,R1上配置PAT实现内网对Internet的访问.
2:两台防火墙之间建立IPSec VPN,连接穿过NAT设备,配置实现两端对等体成功建立IPSec连接.(IP地址自己指定,但尽可能节省公网IP地址)。
三、配置注意事项:
由于PAT设备的外网一侧发起建立管理连接(端口号为500)或是数据连接(端口号为4500),,PAT设备同样无法确定是与内网那个设备建立,会导致连接建立失败,所以需要将端口号500和4500静态映射到内网,具体命令如下:
1:基础配置:
ciscoasa (config-if)# host ASA1
ASA1(config)# int e0/0
ASA1(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
ASA1(config-if)# ip add 192.168.1.254 255.255.255.0
ASA1(config-if)# no sh
ASA1(config-if)# int e0/1
ASA1(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
ASA1(config-if)# ip add 192.168.2.1 255.255.255.0
ASA1(config-if)# no sh
R1(config)#int f1/0
R1(config-if)#ip add 192.168.2.2 255.255.255.0
R1(config-if)#no sh
R1(config-if)#int f0/0
R1(config-if)#ip add 12.0.0.1 255.255.255.0
R1(config-if)#no sh
R2(config)#int f0/0
R2(config-if)#ip add 12.0.0.2 255.255.255.0
R2(config-if)#no sh
R2(config-if)#int f1/0
R2(config-if)#ip add 23.0.0.2 255.255.255.0
R2(config-if)#no sh
ASA2(config)# int e0/1
ASA2(config-if)# nameif outside
ASA2(config-if)# ip add 23.0.0.3 255.255.255.0
ASA2(config-if)# no sh
ASA2(config-if)# int e0/0
ASA2(config-if)# nameif inside
ASA2(config-if)# ip add 172.16.1.254 255.255.255.0
ASA2(config-if)# no sh
ASA1(config)# route outside 0 0 192.168.2.2
ASA1(config)# access-list haha permit icmp any any
ASA1(config)# access-group haha in interface outside
R1(config)#ip route 0.0.0.0 0.0.0.0 12.0.0.2
R1(config)#ip route 192.168.1.0 255.255.255.0 192.168.2.1
ASA2(config)# route outside 0 0 23.0.0.2
ASA2(config)# access-list haha permit icmp any any
ASA2(config)# access-group haha in interface outside
R1(config)#access-list 101 deny ip 192.168.1.0 0.0.0.255 172.16.1.0 0.0.0.255
R1(config)#access-list 101 permit ip 192.168.1.0 0.0.0.255 any
R1(config)#int f1/0
R1(config-if)#ip nat inside
R1(config-if)#int f0/0
R1(config-if)#ip nat outside
R1(config)#ip nat inside source list 101 interface f0/0 overload
ASA2(config)# nat (inside) 1 0 0
ASA2(config)# global (outside) 1 interface
INFO: outside interface address added to PAT pool
//私网上公网没问题,下来用VPN实现两个私网通信.
ASA1(config)# access-list 200 permit ip 192.168.1.0 255.255.255.0 172.16.1.0
255.255.255.0
ASA1(config)# crypto isakmp enable outside
ASA1(config)# crypto isakmp policy 10
ASA1(config-isakmp-policy)# authentication pre-share
ASA1(config-isakmp-policy)# encryption des
ASA1(config-isakmp-policy)# hash md5
ASA1(config-isakmp-policy)# group 2
ASA1(config-isakmp-policy)# exit
ASA1(config)# crypto isakmp key cisco address 23.0.0.3
ASA1(config)# crypto ipsec transform-set mytrans esp-des esp-md5-hmac
ASA1(config)# crypto map mymap 10 set peer 23.0.0.3
ASA1(config)# crypto map mymap 10 set transform-set mytrans
ASA1(config)# crypto map mymap 10 match address 200
ASA1(config)# crypto map mymap interface outside
ASA2(config)# access-list 200 permit ip 172.16.1.0 255.255.255.0 192.168.1.0 255.255.255.0
ASA2(config)# crypto isakmp enable outside
ASA2(config)# crypto isakmp policy 10
ASA2(config-isakmp-policy)# authentication pre-share
ASA2(config-isakmp-policy)# encryption des
ASA2(config-isakmp-policy)# hash md5
ASA2(config-isakmp-policy)# group 2
ASA2(config-isakmp-policy)# exit
ASA2(config)# crypto isakmp key cisco address 12.0.0.1
ASA2(config)# crypto ipsec transform-set mytrans esp-des esp-md5-hmac
ASA2(config)# crypto map mymap 10 set peer 12.0.0.1
ASA2(config)# crypto map mymap 10 set transform-set mytrans
ASA2(config)# crypto map mymap 10 match address 200
ASA2(config)# crypto map mymap interface outside
ASA2(config)# access-list no-nat permit ip 172.16.1.0 255.255.255.0 192.168.1.0 255.255.255.0
ASA2(config)# nat (inside) 0 access-list no-nat
R1(config)#ip nat inside source static udp 192.168.2.1 500 interface f0/0 500
R1(config)#ip nat inside source static udp 192.168.2.1 4500 interface f0/0 4500
测试:
1.C:\>ping 192.168.1.1
Pinging 192.168.1.1 with 32 bytes of data:
Reply from 192.168.1.1: bytes=32 time=65ms TTL=128
Reply from 192.168.1.1: bytes=32 time=36ms TTL=128
Reply from 192.168.1.1: bytes=32 time=46ms TTL=128
Reply from 192.168.1.1: bytes=32 time=42ms TTL=128
Ping statistics for 192.168.1.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 36ms, Maximum = 65ms, Average = 47ms
2.ASA2# sho crypto isakmp sa
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 12.0.0.1
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE
3.ASA2# sho crypto ipsec sa
interface: outside
Crypto map tag: mymap, seq num: 10, local addr: 23.0.0.3
access-list 200 permit ip 172.16.1.0 255.255.255.0 192.168.1.0 255.255.255.0
local ident (addr/mask/prot/port): (172.16.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0)
current_peer: 12.0.0.1
#pkts encaps: 7, #pkts encrypt: 7, #pkts digest: 7
#pkts decaps: 7, #pkts decrypt: 7, #pkts verify: 7
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 7, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 23.0.0.3/4500, remote crypto endpt.: 12.0.0.1/4500
path mtu 1500, ipsec overhead 66, media mtu 1500
current outbound spi: 164EF763
inbound esp sas:
spi: 0xBAC6472B (3133556523)
transform: esp-des esp-md5-hmac none
in use settings ={L2L, Tunnel, NAT-T-Encaps, }
slot: 0, conn_id: 4096, crypto-map: mymap
sa timing: remaining key lifetime (kB/sec): (4274999/28704)
IV size: 8 bytes
replay detection support: Y
outbound esp sas:
spi: 0x164EF763 (374273891)
transform: esp-des esp-md5-hmac none
in use settings ={L2L, Tunnel, NAT-T-Encaps, }
slot: 0, conn_id: 4096, crypto-map: mymap
sa timing: remaining key lifetime (kB/sec): (4274999/28703)
IV size: 8 bytes
replay detection support: Y
本站内容不得转载,违者必究!本站关键词:苏州思朋,苏州CCNP,CCNP培训,项目拓扑